|
| AVAYA Installati |
Thursday, March 22, 2007
Friday, August 13, 2004
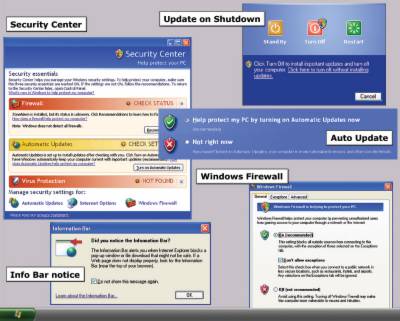
Windows Update - XP SP2
<--My Recovered Blog -->
http://www.pcmag.com/article2/0,1759,1632981,00.asp
posted by _[ n S r ]_ at 12:24 PM
http://www.pcmag.com/article2/0,1759,1632981,00.asp
Operating systems just ain't what they used to be. For a while, Microsoft released a new version of Windows every two or three years—each creating a ripple effect on how we all used and thought about technology. But now, there's a long wait on. It looks like we won't see even a widespread preview of the next major version of Windows, code-named Longhorn, until the first half of next year; and we'll be waiting for a shipping version until at least 2006 or 2007. That's more than five years after Windows XP shipped in October 2001. Meanwhile, questions are swirling about what will be in Longhorn, and even about whether any new version of Windows can really change the way we use computers.
The very success of Windows—it's now on over 90 percent of desktop PCs—has created a technology monoculture that is both resistant to change and a target for malicious hackers. One reason for Longhorn's delay is that all of the recent threats against Windows made Microsoft realize that customers needed more immediate help. As a result, Microsoft focused more on adding new security features to Windows XP Service Pack 2 and getting it out the door (which should happen very shortly). "We actually had to reallocate resources and programmers who were on the Longhorn team to work on SP2," says Greg Sullivan, a lead Windows product manager. Microsoft was making these moves at the same time criticism was raining down on it for the role Windows has played in permitting the propagation of viruses and other computing threats. (For more on this subject, see "Is Microsoft to Blame?" in our August 3 issue.)
In addition to improving security in the underlying Windows code, SP2 will include several enhancements that make it easier for users to configure their systems to be safe—and stay safe. SP2 will automate the installation of critical security patches and turn on an improved firewall by default, and it will include a new security center to monitor the status of OS updates as well as your antivirus and firewall. It also has features that IT managers can use to customize security in enterprises and small businesses.
Because SP2 is the most significant update to Windows that Microsoft plans to release before Longhorn arrives, beta testers are scrutinizing it closely. Some have reported potential compatibility and support problems stemming from the new firewall and automated updates. "Many people are worried about it," says Tom Stachowiak, one of the beta testers, "but it works pretty well. I've run into only one minor compatibility problem. While this may not stop all our security woes, it's a big step forward. My system also runs a lot faster."
The very success of Windows—it's now on over 90 percent of desktop PCs—has created a technology monoculture that is both resistant to change and a target for malicious hackers. One reason for Longhorn's delay is that all of the recent threats against Windows made Microsoft realize that customers needed more immediate help. As a result, Microsoft focused more on adding new security features to Windows XP Service Pack 2 and getting it out the door (which should happen very shortly). "We actually had to reallocate resources and programmers who were on the Longhorn team to work on SP2," says Greg Sullivan, a lead Windows product manager. Microsoft was making these moves at the same time criticism was raining down on it for the role Windows has played in permitting the propagation of viruses and other computing threats. (For more on this subject, see "Is Microsoft to Blame?" in our August 3 issue.)
In addition to improving security in the underlying Windows code, SP2 will include several enhancements that make it easier for users to configure their systems to be safe—and stay safe. SP2 will automate the installation of critical security patches and turn on an improved firewall by default, and it will include a new security center to monitor the status of OS updates as well as your antivirus and firewall. It also has features that IT managers can use to customize security in enterprises and small businesses.
Because SP2 is the most significant update to Windows that Microsoft plans to release before Longhorn arrives, beta testers are scrutinizing it closely. Some have reported potential compatibility and support problems stemming from the new firewall and automated updates. "Many people are worried about it," says Tom Stachowiak, one of the beta testers, "but it works pretty well. I've run into only one minor compatibility problem. While this may not stop all our security woes, it's a big step forward. My system also runs a lot faster."
posted by _[ n S r ]_ at 12:24 PM
Sunday, August 1, 2004
XP SP2 - at your service?
<--My Recovered Blog -->
http://comment.zdnet.co.uk/0,39020505,39164508,00.htmby Leader
ZDNet UK August 25, 2004, 11:40 BST
Automatic update doesn't mean you have to update automatically.
It was supposed to solve the gaping holes in Windows XP's defences almost at a stroke, and in the run-up to its August 2004 launch Microsoft promised an unrelenting campaign to persuade businesses and individuals to upgrade at the earliest opportunity. But the optimism surrounding Service Pack 2 (SP2) is leaking away by the day.
From today, Microsoft is downloading SP2 into computers that have XP's Automatic Update feature turned on. But such has been the apprehension among IT managers about the 80-100MB upgrade flooding into their users' desktops that Microsoft was forced to issue a tool that temporarily blocks the auto-update feature. This is supposed to give businesses more time to test their internal applications for compatibility. More than 40 applications (including several of Microsoft's own) have so far been identified as breaking under SP2, although many of these are mended simply by opening the relevant port in the new Windows Firewall (which is turned on by default in SP2).
There have also been questions raised about the quality of Windows Firewall (specifically, it lacks outbound blocking, which protects against spyware and is supported by almost all third-party firewalls). Meanwhile, security flaws are beginning to emerge in SP2 that will sow further seeds of doubt in the minds of potential upgraders.
So is SP2 more of a spent round than a magic bullet? Clearly, there are a lot of useful new features in SP2 and it's free, so once you've made sure that all your applications work under it, there's little reason to give it the cold shoulder. But equally clearly, it's no panacea, and unless Windows can overhaul some of its evolutionary baggage to make it less structurally susceptible to malware of all kinds, then it's still going to catch a cold on a regular basis.
If Service Pack 2 turns out, as is likely, to be a plucky but ultimately doomed stand against the forces of darkness, what's next? In the short term, we'll have to carry on regularly patching our systems to counter new threats -- and SP2 will help in this respect. Perhaps Longhorn will provide Windows with a fully functional immune system, but getting there might involve even more delay and a longer list of incompatible applications than Microsoft may feel comfortable with.
What's certain is that the question marks against Windows' security aren't going away anytime soon, and sensible companies and individuals should be evaluating all OS alternatives in the meantime.
ZDNet UK August 25, 2004, 11:40 BST
Automatic update doesn't mean you have to update automatically.
It was supposed to solve the gaping holes in Windows XP's defences almost at a stroke, and in the run-up to its August 2004 launch Microsoft promised an unrelenting campaign to persuade businesses and individuals to upgrade at the earliest opportunity. But the optimism surrounding Service Pack 2 (SP2) is leaking away by the day.
From today, Microsoft is downloading SP2 into computers that have XP's Automatic Update feature turned on. But such has been the apprehension among IT managers about the 80-100MB upgrade flooding into their users' desktops that Microsoft was forced to issue a tool that temporarily blocks the auto-update feature. This is supposed to give businesses more time to test their internal applications for compatibility. More than 40 applications (including several of Microsoft's own) have so far been identified as breaking under SP2, although many of these are mended simply by opening the relevant port in the new Windows Firewall (which is turned on by default in SP2).
There have also been questions raised about the quality of Windows Firewall (specifically, it lacks outbound blocking, which protects against spyware and is supported by almost all third-party firewalls). Meanwhile, security flaws are beginning to emerge in SP2 that will sow further seeds of doubt in the minds of potential upgraders.
So is SP2 more of a spent round than a magic bullet? Clearly, there are a lot of useful new features in SP2 and it's free, so once you've made sure that all your applications work under it, there's little reason to give it the cold shoulder. But equally clearly, it's no panacea, and unless Windows can overhaul some of its evolutionary baggage to make it less structurally susceptible to malware of all kinds, then it's still going to catch a cold on a regular basis.
If Service Pack 2 turns out, as is likely, to be a plucky but ultimately doomed stand against the forces of darkness, what's next? In the short term, we'll have to carry on regularly patching our systems to counter new threats -- and SP2 will help in this respect. Perhaps Longhorn will provide Windows with a fully functional immune system, but getting there might involve even more delay and a longer list of incompatible applications than Microsoft may feel comfortable with.
What's certain is that the question marks against Windows' security aren't going away anytime soon, and sensible companies and individuals should be evaluating all OS alternatives in the meantime.
<-- End of My Recovered Blog -->
NTT DoCoMo, Motorola to Develop 3G FOMA Handset
<--My Recovered Blog -->
http://www.physorg.com/news931.html
August 25, 2004
NTT DoCoMo, Inc., Motorola Inc. and Motorola Japan Ltd. announced today that they have signed an agreement to jointly develop a FOMA(R) handset targeting business users by taking advantage of high-speed 3G FOMA technologies. Commercialization is scheduled for spring 2005. The new handset, which is compatible with GSM/GPRS technologies, will be the first FOMA model that may be used outside of Japan.
Unlike i-mode(R)-capable phones, the handset will enable access to the internet through mopera(R) or any other available internet connection service. What's more, its browser will be able to display standard web pages.
In addition, the new handset will be compatible with public wireless LAN services offered by DoCoMo and other providers, enabling users in hotspots to enjoy high-speed internet access at fixed rates.
FOMA: Freedom of Mobile Multimedia Access, DoCoMo's brand name for 3G services, based on the W-CDMA format. Introductory FOMA services for a limited number of users began at the end of May 2002, with full commercial services due in October 2002.
The handset can also be used to view e-mail attachments created in formats such as Microsoft(R) Word, Microsoft(R) Excel, PowerPoint(R). The model will support Bluetooth(R) connectivity for remote control via a laptop or PDA for dialup to the internet, or for convenient hands-free operation using a headset. In addition, the phone will be compatible with PIM (Personal Information Management).
"NTT DoCoMo is delighted to team with Motorola to develop an advanced FOMA handset that meets the special needs of business users, which differ from those of general users," said NTT DoCoMo's Executive Vice President Kei-ichi Enoki.
"In particular, the phone can connect to public high-speed wireless LAN networks to browse the internet and receive e-mail. It also opens a variety of attached documents in their original formats and even works on mobile networks outside Japan. We believe that the new market aimed at business people will join the existing i-mode market in seeing a future expansion," he added.
"Motorola is proud to bring our 3G expertise to this partnership with NTT DoCoMo. This device perfectly embodies our mission to enable users to have a personal hub of communications in the palm of their hand," said Patrick S. Kung, Corporate Vice President, Motorola Inc., General Manager, PCS North Asia.
"This FOMA handset will help business users to multi-task and be more efficient, especially when traveling outside Japan, because they can use the phone and all its features anywhere in the world while staying connected to Japan," he said.
About i-mode:
I-MODE - A packet-based means of wireless data transfer used widely in Japan and offered by Japanese mobile phone company NTT DoCoMo. iMode uses CWML (Compact Wireless Markup Language) instead of WAP's WML for data display. i-Mode was introduced in 1999 and was the first method available to browse the Web from a cellular phone.
Source: Motorola, Inc.; NTT DoCoMo
NTT DoCoMo, Inc., Motorola Inc. and Motorola Japan Ltd. announced today that they have signed an agreement to jointly develop a FOMA(R) handset targeting business users by taking advantage of high-speed 3G FOMA technologies. Commercialization is scheduled for spring 2005. The new handset, which is compatible with GSM/GPRS technologies, will be the first FOMA model that may be used outside of Japan.
Unlike i-mode(R)-capable phones, the handset will enable access to the internet through mopera(R) or any other available internet connection service. What's more, its browser will be able to display standard web pages.
In addition, the new handset will be compatible with public wireless LAN services offered by DoCoMo and other providers, enabling users in hotspots to enjoy high-speed internet access at fixed rates.
FOMA: Freedom of Mobile Multimedia Access, DoCoMo's brand name for 3G services, based on the W-CDMA format. Introductory FOMA services for a limited number of users began at the end of May 2002, with full commercial services due in October 2002.
The handset can also be used to view e-mail attachments created in formats such as Microsoft(R) Word, Microsoft(R) Excel, PowerPoint(R). The model will support Bluetooth(R) connectivity for remote control via a laptop or PDA for dialup to the internet, or for convenient hands-free operation using a headset. In addition, the phone will be compatible with PIM (Personal Information Management).
"NTT DoCoMo is delighted to team with Motorola to develop an advanced FOMA handset that meets the special needs of business users, which differ from those of general users," said NTT DoCoMo's Executive Vice President Kei-ichi Enoki.
"In particular, the phone can connect to public high-speed wireless LAN networks to browse the internet and receive e-mail. It also opens a variety of attached documents in their original formats and even works on mobile networks outside Japan. We believe that the new market aimed at business people will join the existing i-mode market in seeing a future expansion," he added.
"Motorola is proud to bring our 3G expertise to this partnership with NTT DoCoMo. This device perfectly embodies our mission to enable users to have a personal hub of communications in the palm of their hand," said Patrick S. Kung, Corporate Vice President, Motorola Inc., General Manager, PCS North Asia.
"This FOMA handset will help business users to multi-task and be more efficient, especially when traveling outside Japan, because they can use the phone and all its features anywhere in the world while staying connected to Japan," he said.
About i-mode:
I-MODE - A packet-based means of wireless data transfer used widely in Japan and offered by Japanese mobile phone company NTT DoCoMo. iMode uses CWML (Compact Wireless Markup Language) instead of WAP's WML for data display. i-Mode was introduced in 1999 and was the first method available to browse the Web from a cellular phone.
Source: Motorola, Inc.; NTT DoCoMo
<-- End of My Recovered Blog -->
Colleges Offer Free or Cheap Online Music
<--My Recovered Blog -->
http://www.reuters.com/newsArticle.jhtml?type=musicNews&storyID=6061840
Wed Aug 25, 2004 12:41 AM ET
posted by _[ n S r ]_ at 6:34 PM 0 comments
<-- End of My Recovered Blog -->
http://www.reuters.com/newsArticle.jhtml?type=musicNews&storyID=6061840
Wed Aug 25, 2004 12:41 AM ET
By Glenn Maffei
WASHINGTON (Hollywood Reporter) - Downloading free music will be a usual order of business for college students returning to classes in the coming weeks, but this school year will be different at 20 universities in one simple but groundbreaking way: It will be legal.
The music industry pledged to continue to sue students who download music without paying, but it also is pushing a new approach in the battle against widespread piracy: encouraging university administrations to subscribe to download services on behalf of students.
A report submitted to Congress on Tuesday by the Joint Committee of the Higher Education and Entertainment Communities, which is co-chaired by the music industry's top lobbyist, Cary Sherman, and Penn State University president Graham Spanier, addresses the industry's efforts in the past year to curb illegal file-sharing, including education, enforcement and the university partnerships. A hearing on the report before the House Judiciary Committee's Subcommittee on Courts, the Internet and Intellectual Property may be held next month.
In the case of Penn State, 15,000 students were given free access in November to download a half-million songs, the first university to start such a program. The university's information-technology fees fund the contract with Napster, a descendent of the company that once threatened the industry's profitability by allowing unsanctioned sharing of music collections.
Now, 20 schools -- including Wake Forest, Tulane, Purdue, and Ohio University -- have climbed on board to give students free or low-cost access to music through a deal with Real Networks' music service Rhapsody. Although students are not be able to keep the music at the end of the school year unless they pay for it, industry and university officials believe that readily providing the music while school is in session takes away the incentive to steal it.
"Ours is clean, it's fast, it's high quality, it's legal," Spanier said.
Meanwhile, the aggressive effort by music industry trade group the Recording Industry Assn. of America (RIAA) to battle unauthorized downloading by suing students, faculty and university employees for copyright infringement continues. As of April, the music industry trade group had filed lawsuits against 135 students, faculty members or employees at 35 universities.
"You have to look at where we're coming from," RIAA president Sherman said. "As little as a year ago, there was still a great deal of reluctance by universities to consider this a problem that they needed to address at all. Now you have universities taking a wide variety of steps to address the problem. ... It introduces students to the concept that music has value and that the people who create it deserve to get paid."
Beyond an interest in discouraging piracy, universities benefit by avoiding tying up "tremendous amounts" of external bandwidth and subjecting computer systems to outside viruses, Sherman said.
WASHINGTON (Hollywood Reporter) - Downloading free music will be a usual order of business for college students returning to classes in the coming weeks, but this school year will be different at 20 universities in one simple but groundbreaking way: It will be legal.
The music industry pledged to continue to sue students who download music without paying, but it also is pushing a new approach in the battle against widespread piracy: encouraging university administrations to subscribe to download services on behalf of students.
A report submitted to Congress on Tuesday by the Joint Committee of the Higher Education and Entertainment Communities, which is co-chaired by the music industry's top lobbyist, Cary Sherman, and Penn State University president Graham Spanier, addresses the industry's efforts in the past year to curb illegal file-sharing, including education, enforcement and the university partnerships. A hearing on the report before the House Judiciary Committee's Subcommittee on Courts, the Internet and Intellectual Property may be held next month.
In the case of Penn State, 15,000 students were given free access in November to download a half-million songs, the first university to start such a program. The university's information-technology fees fund the contract with Napster, a descendent of the company that once threatened the industry's profitability by allowing unsanctioned sharing of music collections.
Now, 20 schools -- including Wake Forest, Tulane, Purdue, and Ohio University -- have climbed on board to give students free or low-cost access to music through a deal with Real Networks' music service Rhapsody. Although students are not be able to keep the music at the end of the school year unless they pay for it, industry and university officials believe that readily providing the music while school is in session takes away the incentive to steal it.
"Ours is clean, it's fast, it's high quality, it's legal," Spanier said.
Meanwhile, the aggressive effort by music industry trade group the Recording Industry Assn. of America (RIAA) to battle unauthorized downloading by suing students, faculty and university employees for copyright infringement continues. As of April, the music industry trade group had filed lawsuits against 135 students, faculty members or employees at 35 universities.
"You have to look at where we're coming from," RIAA president Sherman said. "As little as a year ago, there was still a great deal of reluctance by universities to consider this a problem that they needed to address at all. Now you have universities taking a wide variety of steps to address the problem. ... It introduces students to the concept that music has value and that the people who create it deserve to get paid."
Beyond an interest in discouraging piracy, universities benefit by avoiding tying up "tremendous amounts" of external bandwidth and subjecting computer systems to outside viruses, Sherman said.
<-- End of My Recovered Blog -->
Password Problems Predictable, Preventable
<--My Recovered Blog -->
http://www.securitypipeline.com/trends/29100873
By Keith Ferrell,
Password usage keeps growing, yet widely ignored best-practices mean they're less secure now than ever.
Evidently, men are password pigs.
According to a research group investigating image-based passwords, men tended to pick images of attractive female models. That was predictable--and not just because men are. Predictability itself, in many forms, is one of the biggest password challenges.
That's been true since the earliest days of computing, and is no less so today, despite plenty of readily available, solid password advice.
Yet most of us still make our passwords the old-fashioned way--creating one password per identification-required account, probably using a recognizable word or number sequence. Worse yet, but even more predictable, many of us keep that same password for extended periods of time. How many of us have had the same password for the same account for months? Years?
Even scrupulously following password best practices is no guarantee that your secret word will remain yours alone. Not in this age of keystroke loggers on the prowl for passwords and PINs.
It's hard to say when technology will be able to solve the password problem. Biometric passports have faced trouble crossing hurdles in the real world, and there's no reason to expect that fingerprint and other physical identifiers will make a more rapid leap to our desktops.
Likewise, the growing array of sophisticated access management suites may offer some authentication relief to enterprises that deploy them, but don't look for widespread implementation right away.
Meanwhile, the gathering e-commerce enthusiasm for single sign-on solutions is matched by a rising chorus citing SSO's problems.
Suppose all of the technical problems were overcome, though, and all of the hackers and phishers went away? Would that solve the password problem?
Probably not. Human nature being what it is, a substantial percentage of us just won't be able to keep our passwords secret, no matter how badly we need to. After all, three-quarters of the people surveyed recently admitted that they would gladly swap their password for chocolate.
Which just goes to show that, sure, men may be pigs when it comes to passwords, but few secrets are safe when anyone's sweet tooth is tempted.
posted by _[ n S r ]_ at 2:50 AM 0 comments
<--My Recovered Blog -->
http://www.securitypipeline.com/trends/29100873
By Keith Ferrell,
Password usage keeps growing, yet widely ignored best-practices mean they're less secure now than ever.
Evidently, men are password pigs.
According to a research group investigating image-based passwords, men tended to pick images of attractive female models. That was predictable--and not just because men are. Predictability itself, in many forms, is one of the biggest password challenges.
That's been true since the earliest days of computing, and is no less so today, despite plenty of readily available, solid password advice.
Yet most of us still make our passwords the old-fashioned way--creating one password per identification-required account, probably using a recognizable word or number sequence. Worse yet, but even more predictable, many of us keep that same password for extended periods of time. How many of us have had the same password for the same account for months? Years?
Even scrupulously following password best practices is no guarantee that your secret word will remain yours alone. Not in this age of keystroke loggers on the prowl for passwords and PINs.
It's hard to say when technology will be able to solve the password problem. Biometric passports have faced trouble crossing hurdles in the real world, and there's no reason to expect that fingerprint and other physical identifiers will make a more rapid leap to our desktops.
Likewise, the growing array of sophisticated access management suites may offer some authentication relief to enterprises that deploy them, but don't look for widespread implementation right away.
Meanwhile, the gathering e-commerce enthusiasm for single sign-on solutions is matched by a rising chorus citing SSO's problems.
Suppose all of the technical problems were overcome, though, and all of the hackers and phishers went away? Would that solve the password problem?
Probably not. Human nature being what it is, a substantial percentage of us just won't be able to keep our passwords secret, no matter how badly we need to. After all, three-quarters of the people surveyed recently admitted that they would gladly swap their password for chocolate.
Which just goes to show that, sure, men may be pigs when it comes to passwords, but few secrets are safe when anyone's sweet tooth is tempted.
posted by _[ n S r ]_ at 2:50 AM 0 comments
<--My Recovered Blog -->
Subscribe to:
Posts (Atom)